Staying safe online is more important than ever. A recent study found that a cyber attack occurs every 39 seconds.
What are the attackers after? Your personal information and data - which is very valuable!
Recognizing online threats is key to protecting your privacy, finances, and even your identity.
Phishing
Phishing is when someone tries to trick you into giving them valuable information like your bank account or credit card number. The attackers will often send you an email or message with what looks like a legitimate website.
How to avoid phishing attacks:
Avoid clicking links in emails or messages from people you do not know.
Don't give out personal information unless you trust the person.
Example of a phishing attempt:
The sender is trying to trick the recipient into entering confidential information.
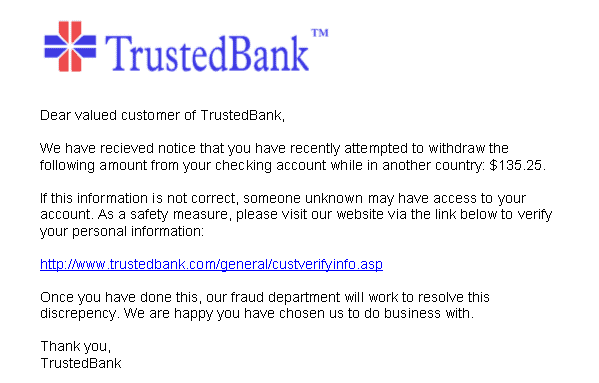 Image source: Public Domain
Image source: Public Domain
Quiz
Which of these is a clue that the email from TrustedBank might be a phishing attempt?
Malware
Malware is a term for any type of malicious software. It's designed to damage, disrupt, or take control of your computer or device.
You may have malware on your device if you notice:
A slow, crashing, or freezing computer
A blue error screen
Programs opening and closing automatically
Increased pop-ups, toolbars, or other unwanted programs
Emails or messages being sent without you prompting them
 The best way to avoid malware is to only download files from sources you trust.
The best way to avoid malware is to only download files from sources you trust.
Quiz
You receive an email with a suspicious link. Should you:
Adware & Spyware
Adware tracks your browsing habits with your permission, it:
Is installed when you download certain programs (usually free software).
Can cause unwanted pop-ups.
May slow down your computer.
Tracks your personal data and shares it with companies.
Spyware is similar to adware but is installed without your permission.
It may track your typing to collect personal information, such as passwords and credit card numbers.
Consider This Scenario
Sara receives an email that appears to be from her boss. The email asks her to purchase some gift cards as prizes for the team meeting later that afternoon.
Sara heads to the store and uses her credit card to purchase the gift cards. She then responds to the email with the gift card codes.
When Sara talks to her boss later that afternoon, her boss has no knowledge of this email conversation.
Quiz
What could Sara have done to protect herself from this online risk?
Protect Yourself Online
How to protect yourself online:
Make sure your antivirus program is up to date
Do not click on links from people you do not know or trust
Do not download suspicious files
Make sure your browser is up to date
Read privacy policies before giving your consent
Make sure your computer or mobile device has the latest security updates
Take Action
Cyber attacks are becoming more common and sophisticated. The best thing you can to do protect yourself in the digital environment is to be prepared.
Remember:
Phishing - tricks you into clicking a bad link
Malware - software that attempts to damage your computer
Adware - tracks your browsing habits
Spyware - tracks your typing to steal personal information
How can you use this information to better protect yourself online?
 Photo by rupixen.com on Unsplash
Photo by rupixen.com on UnsplashYour feedback matters to us.
This Byte helped me better understand the topic.
